kescherDNS is a DNSSEC-validating DNS resolver for public use.
This service used to be inspired by Mozilla's push of DNS-over-HTTPS in their own browser, with them setting Cloudflare as the default provider in the settings.
Cloudflare is a US-based provider of various internet services, most of which aim to make them a monopoly for accessing resources on the visible web (which they have since become for 20% of it).
Another popular provider is Google, which, for obvious reasons, is also not a good choice due to privacy concerns.
However, abandoning encrypted DNS connections just because of several providers of this service being bad is not exactly a great alternative.
Therefore, originally, this service used to provide DNS-over-HTTPS and DNS-over-HTTPS only. As of 2022, we are also open to unencrypted connections,
but with some limitations to prevent reflection-amplification attacks.
This DNS service has been set up specifically to be as privacy-friendly as possible.
We don't permanently log queries or source IP addresses. However, we do keep of query counts per IP, per second, in memory, for automatic rate limiting/enforcing a TCP connection (reflection-amplification attack mitigation). We also have a cache for repeated DNS requests, in order to be nice to authoritative DNS servers around the world.
We do not set or forward ECS (EDNS Client Subnet) information, except for the domains authoritatively hosted on the same servers (kescher.at).
For these, logging is disabled entirely, and this info is only used for GeoIP purposes (so from the servers I own, you get the closest to you as determined by your IP or resolver IP).
The resolver, behind the scenes, actively probes all authoritative nameservers for DNS-over-TLS support. If a server does support DNS-over-TLS, communication will be done using DNS-over-TLS.
This means that less of the queries sent to us end up leaking on an unencrypted connection.
DNSCrypt, unfortunately, runs on the same TCP port as HTTPS does: 443. This means it is very annoying to configure DNSCrypt on its proper port on a server that has any other services running. I could technically host a DNSCrypt service on another port, but I dislike running services on non-default ports. I have tried doing this with SSH before, which came with too many drawbacks for me to consider it viable.
Currently, the following DNS services:
dns.kescher.at / kalos.kescher.at: 89.58.18.85 / 2a0a:4cc0:0:f31::1dns.kescher.at / unova.kescher.at: 45.129.181.164 / 2a03:4000:47:8b::1dns.kescher.at is usable for all hosts.
Firefox has a dedicated section for configuring DNS-over-HTTPS. This makes it very easy to configure it for use with kescherDNS.
about:preferences#privacy into the address bar.https://dns.kescher.at/dns-query into the text field that appears below the dropdown.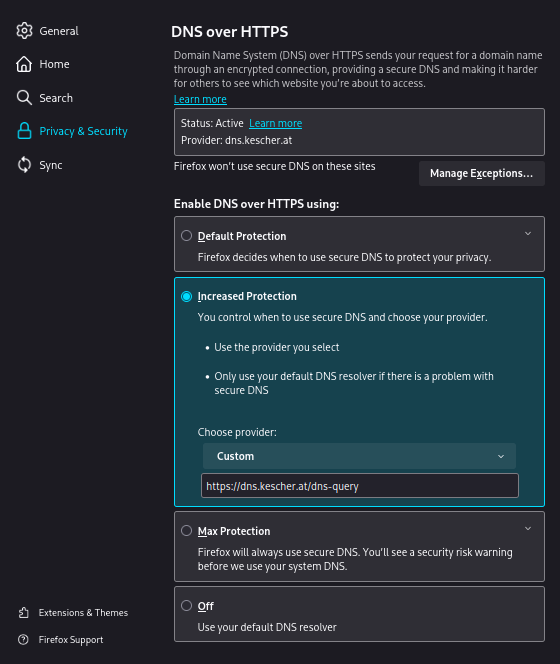
Note: This may not work on all Chromium-based browsers.
Chromium-based browsers should have a section that makes it easy to configure kescherDNS using DoH.
chrome://settings/security into the address bar / omnibox.https://dns.kescher.at/dns-query into the unlabelled text field below the dropdown.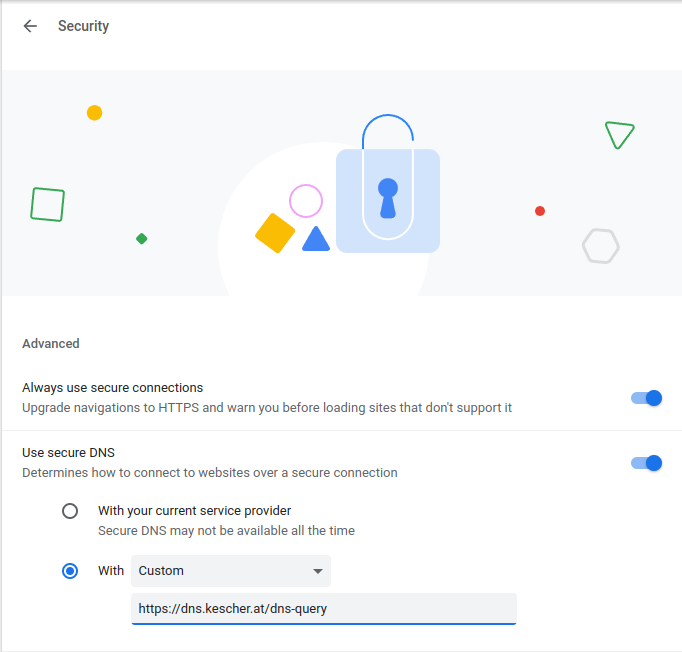
If you use Unbound as resolver, you can easily add kescherDNS with DoT. All you have to do is add this to your config:
forward-zone: name: "." forward-addr: 2a0a:4cc0:0:f31::1@853#kalos.kescher.at forward-addr: 89.58.18.85@853#kalos.kescher.at forward-addr: 2a03:4000:47:8b::1@853#unova.kescher.at forward-addr: 45.129.181.164@853#unova.kescher.at